OAuth2 and OpenId as a service
Note
For this kind of SSO integration, the data is exchanged between your applications and Qualifio via secure server-to-server calls performed in the back-end.
Campaigns Participation flow
With this technique, participants start the campaign regardless of their connection/identification status
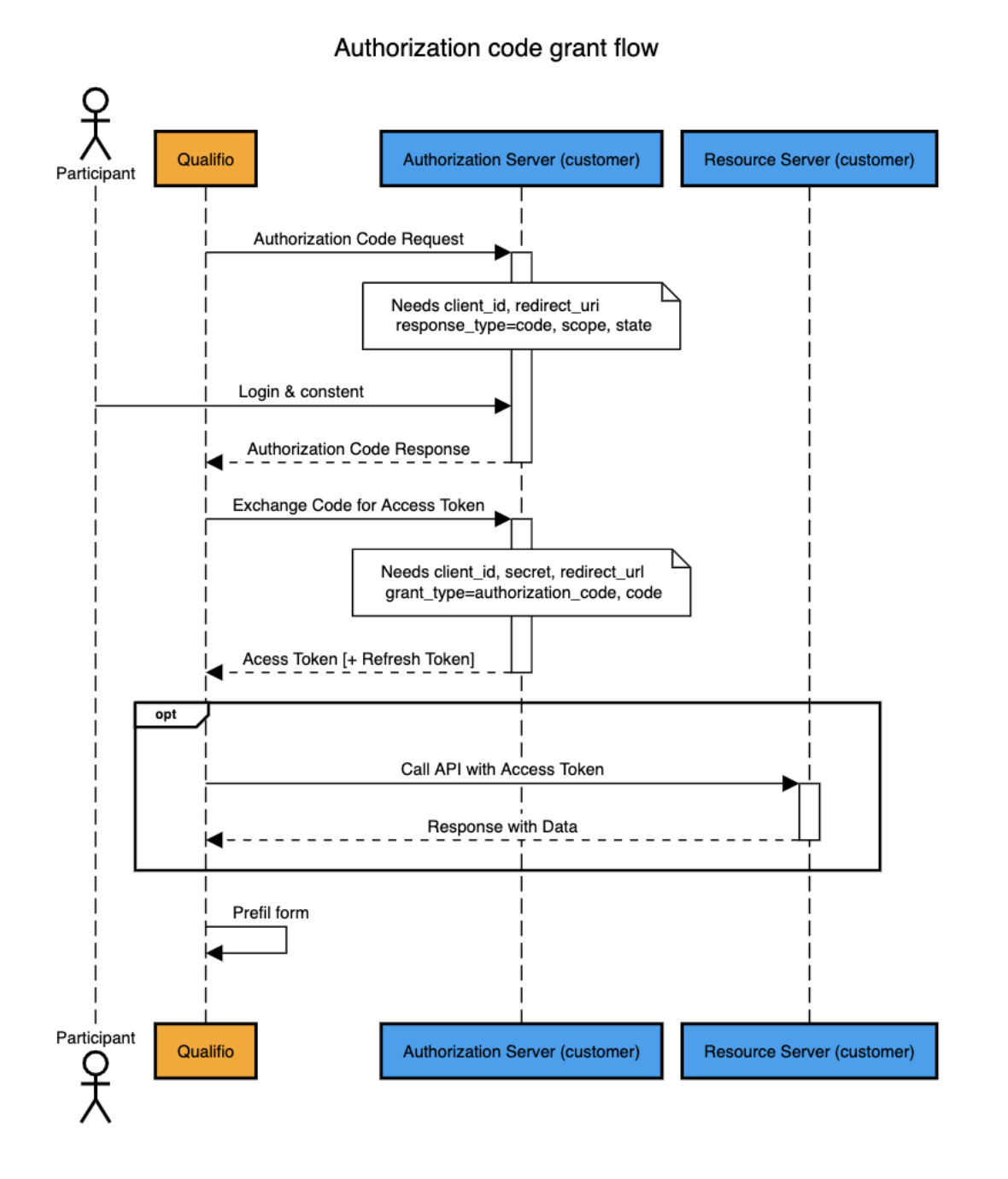
- At the form step, the participant is redirected to the authorization URL (log-in/pre-registration/consent) provided by the customer. The authorization URL includes parameters such as :
- client_id : customer application ID
- redirect_uri: oauth service's URL to which the participant has to be redirected back after his/her authentication/registration.
- scope : defines Qualifio’s access rights when accessing your database. E.g.: Qualifio is allowed to get profile information (email, firstname, lastname, address…), update the profile….
- Ex:
openid%20email%20profile
- Ex:
- state : state token including information to recover the session on Qualifio side
- Once the user is redirected back to the Qualifio Oauth service, the service will read the state parameter to finally redirect the user to the Qualifio campaign, where he previously left (thanks to the redirect uri).
- After being redirected back to the campaign, the SSO connection will execute a token request to redeem the authorization code (received as request parameter) from the access token.
- Qualifio gets the participant's profile by either reading data directly from the JWT access token or by querying the REST API (ex: get profile) with the access token.
- Based on this information, Qualifio will prefill the identification form with the data in the participant's profile.
- After the identification form is submitted by the participant, the profile's data will be stored in the campaign's statistics.
Process flow
What are the requirements to set it up?
You have to own an Authorization Server supporting the OpenID specification to use this technique. Numerous vendors and SaaS platforms offer such support such as Okta, Auth0, Gygia to name only a few of them.
- You need to host the login page. This login screen allows participants to create a new account or login.
- The Authorization Server has to handle the following information:
- Client_id: to be shared with Qualifio
- Redirect_uri: parameter will be filled with the Qualifio oauth service's URL to which the participant has to be redirected back after his authentication/registration (code and state parameters will be appended to the redirect URL by your authorization service); always the value https://player.qualifio.com/oauth/callback
- Scope (optional): to be shared with Qualifio
- State: used by Qualifio to restore the participant status after the login process (Provided by Qualifio)
- The Authorization Server has to handle the following information:
- You have a resource server able to send a JWT. This JWT should contain:
- Access_token: used to call your API and get profile information
- Directly the profile information
tip
Qualifio Redirect_uri is: https://player.qualifio.com/oauth/callback
Notes
- Standard protocol based on server to server communication. Therefore, this method comes with a high level of security explaining why it is used and supported by enterprises like Google or Facebook. This is why Qualifio strongly recommends this method
- You have your own authentication process using Oauth2/OpendID protocol, coming with a login/register/forgot my password screen on a dedicated page or a login/register popin available.