SSO Standards
What is a single-sign-on flow?
If you want to use Qualifio as a reason to identify, meaning increasing the number of profiles in your database via interactive campaigns, building a Single Sign-on (SSO) connection between your application and Qualifio is what you need.
Thanks to an account creation/login process integrated to Qualifio interactive campaigns, you can allow participants to create themselves a profile/personal space on your domain.
Coming with an SSO data connection, Qualifio campaigns help to increase the number of profiles in your database, as well as extend the information collected for existing accounts and/or refresh the ones already stored.
Qualifio offers several types of SSO integrations to its clients. If the implementation is different, their goal is always the same: identify a user and fetch his/her profile’s data to prefill Qualifio form in the context of an identified campaign.
This data can be stored in a personal space accessible by the participant (printscreen) or stored in your application(s) without providing access to it to your audience.
SSO connection flow
In a SSO data connection flow, there are different scenarios when reaching the authentication step (always happening just before the form step):
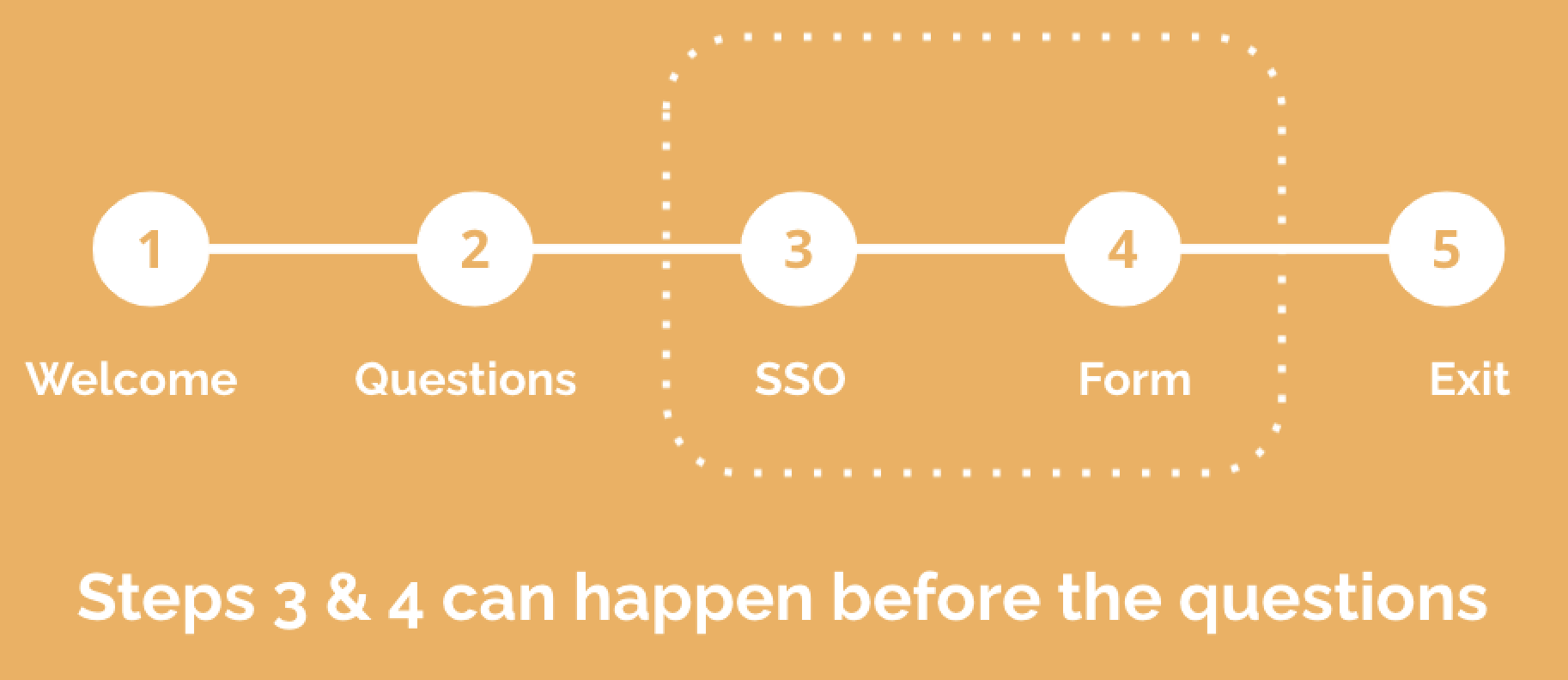
- The participant is already logged in to his/her personal space or identified by you with a personal user ID. He/she can move to the form step, thanks to different technical methods of the SSO connection flow selected. By configuration the form can be pre-filled and displayed or pre-filled and automatically submitted. The participant won’t see the form step displayed.
- The participant is not registered to his/her personal space
- The participant doesn’t exist yet in your database. He/she will have to create a new account to access the personal space (register), in your domain. Once connected, he/she will access the form step.
- The participant does already exist in your database but is not logged-in yet. He/she will have to log-in in your domain (login) before to access the form step.
- The participant does already exist in your database but has forgotten his/her password. He/she has to enter the “forget password” flow in your domain to be able to login. Once connected with the new credentials, he/she will access the form step.
Technical solutions overview
Based on your business (types of campaigns, campaign accessibility…) & technical requirements, Qualifio will propose the best technical solution to handle your different scenarios and therefore ensure the best user experience to campaign’s participants and members.
The purpose of this document is to describe the different techniques used by Qualifio when it comes to an authentication flow:
- OAuth 2 & OpenId as a service
- Works for all connection scenarios (participant logged in or not when the SSO flow starts)
- High degree of security as information is exchanged via secure server-to-server calls in the back-end
- An Authorization Server supporting the OpenID specification is required to use this technique.
- To host a login/register page accessible to the participants
- With a resource server able to send JWT’s to Qualifio
- Exchange by messages
- Works for all connection scenarios (participant logged in or not when the SSO flow starts) - depending on the moment of the exchange chosen
- Lower level of security as messages are exchanged between the Qualifio iframe & the parent page directly in the front-end (i.e. in the participant browser)
- Messages could be exchanged at the campaign load or via bilateral messages between the parent page & the campaign iframe
- Specific functions must be added in pages hosting Qualifio iframes
- Specific CNAME to have campaigns & host pages running on the same subdomain
- Use of JS tag to integrate campaigns with host pages
- Possibility to send JWT’s to Qualifio
- Cookie reader
- Works only if the participant is already registered/logged in when the authentication step starts
- Lower level of security as cookies are exchanged between the Qualifio iframe & the parent page directly in the front-end
- Cookie exchange means :
- Specific CNAME to have campaigns & host pages running on the same subdomain (domain cannot be qualifioapp.com)
- A high dependency towards web browsers’ cookie policy
- This approach can be used on top of the other integration
- Secure token flow
- Works only if the participant is already registered/logged in when the campaign is loaded
- Works when you know your audience and you can associate one unique ID to a participant, coming from one of your tools in the back-end. This solution doesn’t work for lead generation campaigns, where no ID is attributed to the participant prior the campaign launch
- Includes the possibility to apply custom participation limitation rules, also shared via the token
- Development required on your side to enrich campaign URL or JS tag or minisite script, with the secure token, when integrating it
- Different methods to sign the token, as well as the possibility to encrypt it (either via your own encryption protocol or via Qualifio encryption API)
More detailed information can be found in the following sections of this document. Based on the information shared for each technique, you’ll be able to define the one that suits you the best as well as understand their respective ins and outs.
Campaign integration compatibility
| Oauth2 and OpenId as a Service | Share information at the campaign load | Bilateral messages | Cookie Reader | Secure token | |
|---|---|---|---|---|---|
| Tag JS(qualp_) | OK | OK | OK | Ok | OK |
| Mini-site | OK | NOK | NOK | NOK | OK |
| Webview | OK | NOK | NOK | NOK | OK |
| OK | NOK | NOK | NOK | NOK | |
| Iframe HTML | Degraded After login the user in not redirected to the parent page | NOK | NOK | NOK | OK |
| Preview mode | NOK | NOK | NOK | NOK | NOK |
If you want to use a SSO flow in a mobile application, please contact us to discuss how Qualifio can be integrated on your mobile application.